Launching my entrepreneur adventure

As many people in France (27% according to a study conducted by the French Chamber of Industry and Commerce), I wanted to launch my own company during my whole professional life.
With Sentibee, this is now the case. From the very early stage we're at, it looks really promising.
I know that this blog mostly deals with technical subjects and I want to add a bit more topics about entrepreneurship. So let's do it!
TL,DR;
- I'm launching a new company creating a Cyber Threat Intelligence SaaS application for Vulnerability Intelligence
- You can know more about the project on https://www.sentibee.com/
- We want to simplify the process of watching for emerging vulnerabilities and patching decision
- A form is available here to give us your feedback
- We launch an early program to co-construct this product
- You can get in touch with us for the last 2 points
The genesis
While working at my previous position in a Computer Emergency Response Team, I handled information security incidents on a daily basis. A need for intelligence quickly surfaced.
Responding to incidents requires to take swift action on the basis of partial knowledge. To enhance the response time, it is necessary to have a clear overview of what is happening. And having proper Cyber Threat Intelligence helps by allowing to contextualize bits of data by relying on the feedback of past incidents.
So we put a Cyber Threat Intelligence program in place. This allowed us to collect vast amounts of information related to past and ongoing incidents over the world and get a better understanding of the threat actor ecosystem.
Quickly, in 2021, another need would emerge. log4shell, a newly discovered vulnerability affecting log4j wrecked the industry. log4j was an unknown asset for most, yet with overwhelming presence in company IT systems. And log4shell had considerable impact on the affected systems.
It all started with teens messing with rival Minecraft servers and went all the way to remote code execution on virtually anything running Java in the corporate world.
Public reporting on the vulnerability was messy and subsequent exploitation only occurred a few hours after the disclosure. Incidents were happening one after the other. And obviously it happened on Thursday, a few weeks before Christmas when nobody wanted to touch anything in production.
Starting from this event, my team decided to keep a monitor on such disclosures to be able to respond early to this kind of incidents. We developed a platform internally to provide a vulnerability watch service. Since then, we delivered thousands of notices and hundred alerts.
But going through a mean of 110 vulnerabilities a day is tedious. CVE records pose a ton of problems. Let's take an example:
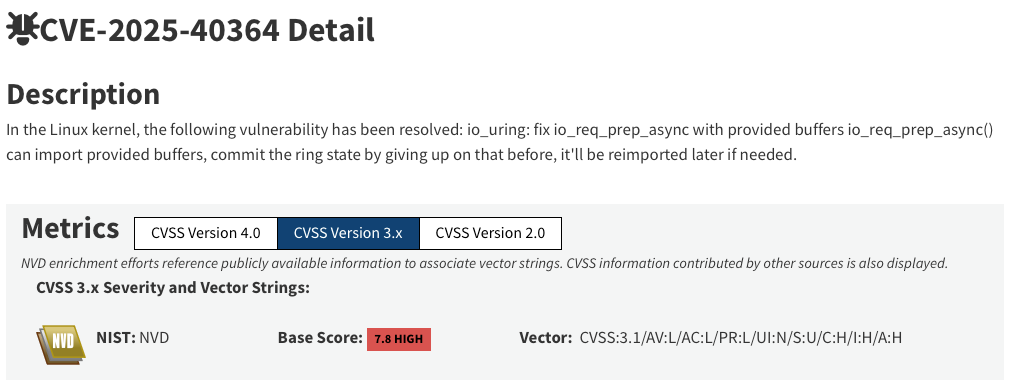
Given this report, more questions rise than are answered:
- Is this vulnerability actually exploited? Even exploitable in a practical context?
- Should we patch it? In which timeline? How?
- Should we consider a high CVSS score as threatening?
And we'll ask these questions a hundred times a day...
Besides, we only want to address vulnerabilities that actually affect our scope taking into account what products matter in it.
It's like pushing the Sisyphus rock all over again everyday.
That is why we had an internal tool to follow only what got us interested. However, we came with some limitations that required extensive investments out of our reach in that context.
Going the entrepreneur way
The timing was right for me and my associate to try something on our own. We had the conviction that this tedious work should not have to be a burden.
What makes a vulnerability dangerous is not only its intrinsic characteristics, it is also and foremost the context: where are the affected assets in the network? what is the probability of an actual exploitation? are these assets mission critical?
And when you talk to a C-level executive, they don't want to know anything about what function in the Linux kernel is affected. They want to know what are the business risks and what they should do about it.
Making this kind of insight accessible to the most is the real value we can add. As reported by the French national information security administration (ANSSI), the exploitation of vulnerabilities is one of the most important attack vectors.
Concentrating the efforts of asset patching on what matters is what allows to prevent a significant part of the incidents.
This is what we wanted to focus on:
- Reducing the noise: no useless alerts, just the essential with proper prioritization
- Making intelligence accessible: we want the small company's IT guy to understand what he should do
- Providing tactical and strategical insights on vulnerabilities: adding context to every single vulnerability to share the stakes and the actual threat
To do that and allow everyone to access such personalized intelligence, we devised that providing a self-service SaaS was necessary to fulfill this mission while allowing prices to stay accessible for any organization.
So we are developing one for the past few months. We want to co-construct it to answer a real need. We already discovered a ton of unfulfilled use cases just by discussing with the community.
This is the objective of our EarlyBee program: onboarding first users and exchanging feedback to provide the best solution for ensuring vulnerability watch.
Go check our website and apply for the EarlyBee program by contacting us!
You can also help us by telling us what are your challenges and expectations on the subject (in French):
I'll let you know how things are going in the future. We are pretty excited to share what we have to propose!

