OpenCTI #6 - Use the data
Discover OpenCTI in this series. This 6th episode will expose features of OpenCTI that allow you to actually use the data.
In the last post we saw the objects that allow to organize everything in the platform in a manner consistent with how the information is related. We saw pretty much everything regarding data input.
Now, it is time to use the data to make it actionable and to make decisions based on it.
Investigate
OpenCTI provides tools to assist in investigations. The investigations pane allows to navigate graphically in the data without actually having to create a Report or a Grouping object.
The investigation pane can be accessed from the top-right menu by clicking on the compass icon.
In general, it will work in a similar fashion compared to the Knowledge tab of the container pages. We won't go into details for filtering options but there are some particularities worth to be mentioned.
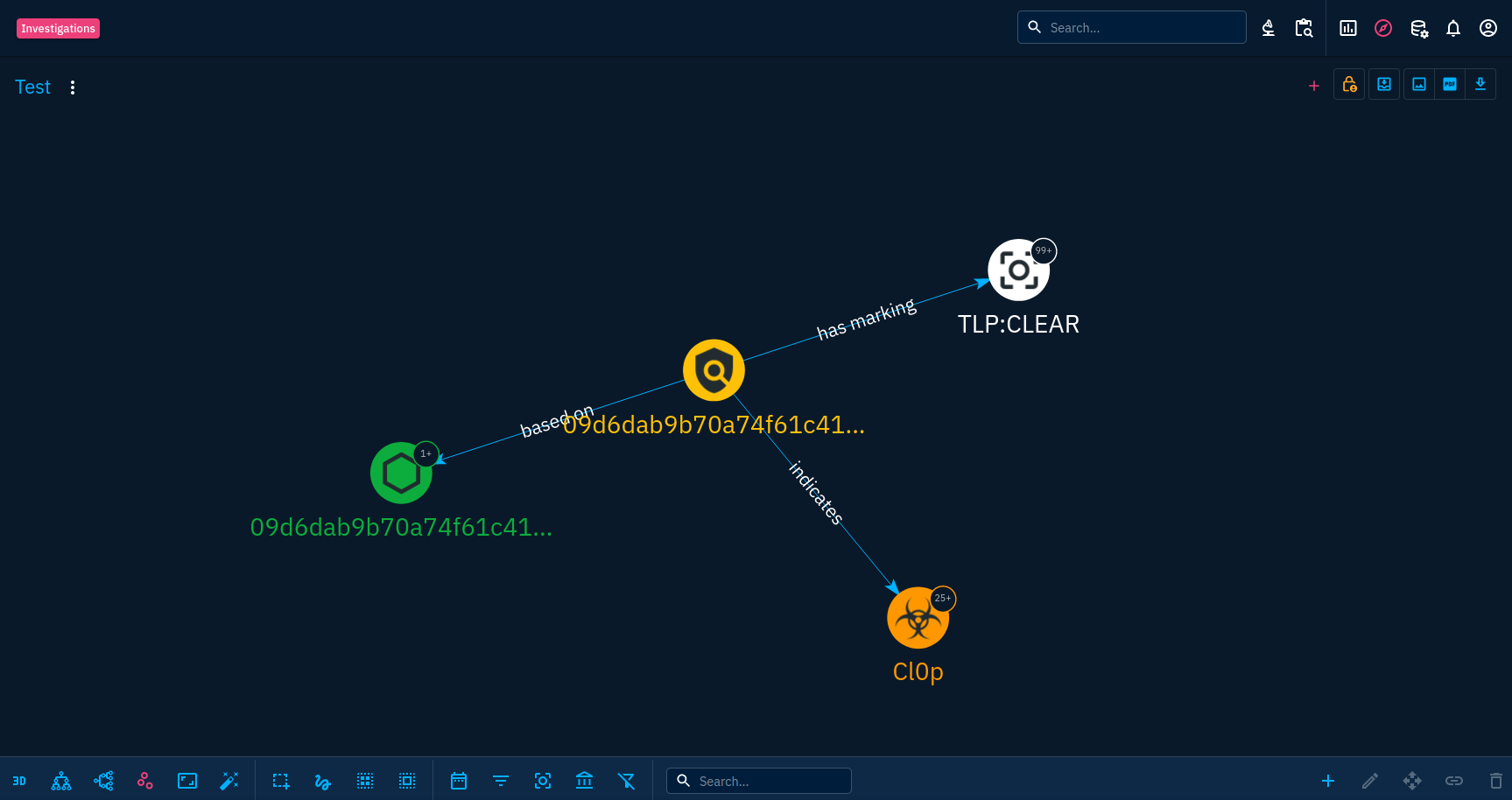
First of all, you will have to add the first object to the investigation. This will be your first pivot point. Let's say you want to do an investigation on Cl0p, it will be a good starting point to add the malware object corresponding to it first.
Of course, you can add more objects in the same way and have several pivot points that are unrelated but the most interesting feature is the expand button located in the bottom-right corner of the screen.
This button allows you to pivot on a node. The number displayed in the bubble associated with the node indicates the number of elements related to the node. On the screenshot above, the Cl0p malware node has more than 25 objects related to it.
Select the pivot point and click on the expand button to include the associated relationships and objects. A pop-up will appear allowing you to filter the objects to add either by object types or relationship types.
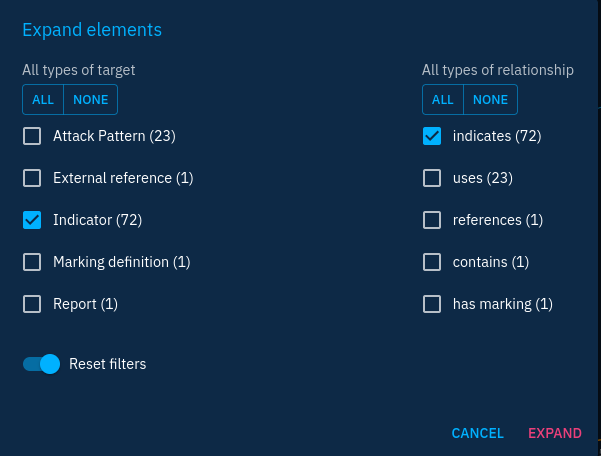
Let's say we would like to add all indicators indicating the malware, we will have the choice between adding Indicator objects and related-to relationships.
Note that the expand feature can add a lot of objects to the investigation in one shot. So keep in mind the number of objects displayed with each type. In the example above, confirming the expansion would include 72 indicator objects in the investigation. This can be a lot. Unfortunately, you cannot be more precise in the filtering of expansion.
You can then use the expand feature of more nodes to elaborate your investigation and hopefully start to see patterns that you can exploit for correlations.
When you're happy with your investigation, you can convert it to a report or a grouping by using the "add to container" or "download as STIX report" buttons at the top-right corner.
What I like to usually do with this view is to go top-down from most general objects to more specific ones. For example, I can start from an intrusion set and go down to the individual domain name observable. Going from this observable, I will run enrichment connectors to get information on the domain name: IP addresses resolved, WHOIS data, etc. This will allow to create other observable objects that are other pivot points.
The investigation tool is a powerful feature that allows to organize ongoing threat hunting or investigation activities.
Sharing data with the external world
In episode 4, we saw that connectors allowed to import and export data from and to OpenCTI. There is another mechanism that allows to import and export data: Ingestion and Data Sharing. Sometimes both are coupled, with a data stream converted on the spot by a connector.
The Ingestion and Data Sharing tabs can be found in the Data module. Ingestion allows to retrieve data from:
- Remote OpenCTI instances with their export stream
- Remote TAXII feeds
- RSS feeds
Data Sharing allows to send data to external parties:
- Live streams: OpenCTI native streams of data that send new data in a continuous flow
- CSV streams: streams in the CSV format for incompatible products
- TAXII collections: expose data on a TAXII server
Ingestion modules are easy to use, specify the required parameters (mostly URLs and authentication) and let them run.
Data sharing modules will most of the time provide filters you can configure to select the data that will be shared. For example, you can include or exclude specific objects: by TLP, object tags, object types, etc...
To allow users to connect to the Data Streams, you must assign authorized users to the stream you create. You can create as many streams as you want, so you can fine-tune the data you wish to send and have complete control over access control.
Usually, I create a unique user for each consumer of a stream and I only grant the permission to access the knowledge.
Conclusion
In this post we saw how the data can be used for investigation and enrichment of the knowledge. We also saw how the data can be shared externally to other tools, notably the ones used by SOCs.
Next, we will go through some more advanced features of OpenCTI.
